Networking & Cloud Computing
azw3 |eng | 2017-10-18 | Author:Adolfo Eloy Nascimento [Nascimento, Adolfo Eloy]
private String softwareId; private String tokenEndpointAuthMethod; private Set<String> responseTypes = new HashSet<>(); private String clientName; private String clientUri; private long clientSecretExpiresAt; Create the following setters (the getters for these fields ...
( Category:
Networking & Cloud Computing
April 13,2018 )
azw3 |eng | 2014-10-31 | Author:Josh Diakun & Paul R Johnson & Derek Mock [Diakun, Josh]
See also The Pivot charting top error codes recipe The Pivoting purchases by geographical location recipe The Pivoting total sales transactions recipe Pivot charting top error codes In this final ...
( Category:
Internet & Social Media
April 13,2018 )
epub |eng | 2017-08-11 | Author:Yohan Wadia
TO create your own KMS key, visit http://docs.aws.amazon.com/lambda/latest/dg/tutorial-env_console.html. With the function deployed, go ahead and configure the SNS trigger for the function. Select the Trigger tab from the AWS Lambda ...
( Category:
Networking & Cloud Computing
April 13,2018 )
epub |eng | 2016-01-30 | Author:Thakurratan, Ranjit Singh
In a cross-vCenter NSX environment, rules created in the Universal Firewall section are replicated to the secondary NSX Managers. To create a Universal Firewall rule, follow these steps: A universal ...
( Category:
Networking & Cloud Computing
April 13,2018 )
epub |eng | 2018-03-20 | Author:Mike Grigsby
PARAMETERS EST DM 1,960.6 EM –297.4 SMS 5,679.4 The fit is much better using fixed effects and the insights from marcom make more sense. E-mail can be negative because of ...
( Category:
Databases & Big Data
April 13,2018 )
epub |eng | | Author:Nan Cheng & Xuemin (Sherman) Shen
57. Xu S, Wang H, Chen T, Huang Q, Peng T (2010) Effective interference cancellation scheme for device-to-device communication underlaying cellular networks. In: Proceedings of IEEE VTC, Ottwa, September 2010 ...
( Category:
Networking & Cloud Computing
April 13,2018 )
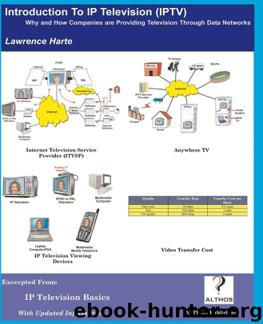
azw3 |eng | 2017-03-25 | Author:Lawrence Harte [Harte, Lawrence]
Broadband Access Systems for IP Television Broadband access systems are networks that can transfer data signals at a rate of 1 Mbps or more. Broadband access systems that can provide ...
( Category:
Software
April 13,2018 )
azw3 |eng | 2015-01-09 | Author:Sean P. Murphy & Sean P. Murphy [Murphy, Sean P.]
Containment, Eradication, and Recovery Phase There is probably no other responsibility of the incident response team that is more important than evidence collection and preservation, which happens primarily in containment. ...
( Category:
Hardware & DIY
April 13,2018 )
epub |eng | | Author:Stamp, Mark
p2,1 = 0.4365 p2,6 = 0.7357 p2,11 = 0.2050 p2,16 = 0.2299 p1,2 = 0.8004 p1,7 = 0.7551 p1,12 = 0.3064 p1,17 = 0.2451 p2,2 = 0.1997 p2,7 = 0.2449 ...
( Category:
Computer Science
April 13,2018 )
azw3 |eng | 2015-09-16 | Author:Wisnu Anggoro & John Torjo [Anggoro, Wisnu]
When we run removework.cpp, compared to blocked.cpp, which will block the program infinitely, the following line of text will be displayed to us: Now, let's dissect the code. As we ...
( Category:
Programming Languages
April 13,2018 )
epub |eng | | Author:Scott Shaw, Andreas François Vermeulen, Ankur Gupta & David Kjerrumgaard
2.Drag the processor icon from the toolbar to the grid to open the Add Processor window, as shown in Figure 6-8. Figure 6-8.Adding a Nifi processor 3.Select the GetTwitter processor ...
( Category:
Networking & Cloud Computing
April 13,2018 )
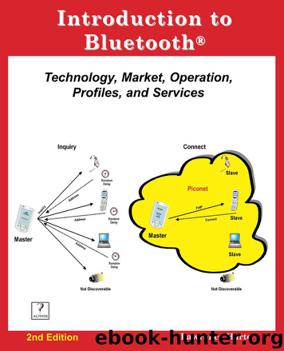
azw3 |eng | 2017-03-09 | Author:Lawrence Harte [Harte, Lawrence]
Figure 1.21, Bluetooth Protocol Reference Model chronous) do not interact with the other protocol layers and directly connect the baseband layer of the device with the upper layer application. Baseband ...
( Category:
Engineering
April 13,2018 )
azw3 |eng | 2016-05-31 | Author:Simon R. Chapple & Eilidh Troup & Thorsten Forster & Terence Sloan [Chapple, Simon R.]
Note Software versions In this chapter, the MPI examples were run on an Apple Mac Book Pro, with a 2.4 GHz Intel Core i5 processor, 8 GB memory, running OS ...
( Category:
Software
April 13,2018 )
azw3, mobi, epub |eng | 2017-06-21 | Author:Giorgio Zarrelli [Zarrelli, Giorgio]
Then there is something we never saw before: | time=0.011048s;;;0.000000;10.000000 This is a pipe, followed by one or more labels, time in our example, and some values usually related to ...
( Category:
Operating Systems
April 13,2018 )
epub |eng | 2016-12-12 | Author:Todd Lammle
Now, let's take a look at the last entry found in the Corp routing table: S* 0.0.0.0/0 is directly connected, FastEthernet0/0 Let's see if the LA router can see this ...
( Category:
Networking & Cloud Computing
April 13,2018 )
Categories
Popular ebooks
The Mikado Method by Ola Ellnestam Daniel Brolund(23444)Kotlin in Action by Dmitry Jemerov(20425)
Grails in Action by Glen Smith Peter Ledbrook(17371)
Sass and Compass in Action by Wynn Netherland Nathan Weizenbaum Chris Eppstein Brandon Mathis(14803)
Configuring Windows Server Hybrid Advanced Services Exam Ref AZ-801 by Chris Gill(7525)
Azure Containers Explained by Wesley Haakman & Richard Hooper(7516)
Running Windows Containers on AWS by Marcio Morales(7067)
Microsoft 365 Identity and Services Exam Guide MS-100 by Aaron Guilmette(5452)
Microsoft Cybersecurity Architect Exam Ref SC-100 by Dwayne Natwick(5291)
Combating Crime on the Dark Web by Nearchos Nearchou(5046)
The Ruby Workshop by Akshat Paul Peter Philips Dániel Szabó and Cheyne Wallace(4723)
Management Strategies for the Cloud Revolution: How Cloud Computing Is Transforming Business and Why You Can't Afford to Be Left Behind by Charles Babcock(4569)
Ember.js in Action by Joachim Haagen Skeie(4310)
Python for Security and Networking - Third Edition by José Manuel Ortega(4298)
The Age of Surveillance Capitalism by Shoshana Zuboff(4279)
Learn Windows PowerShell in a Month of Lunches by Don Jones(4220)
Learn Wireshark by Lisa Bock(4192)
The Ultimate Docker Container Book by Schenker Gabriel N.;(3940)
DevSecOps in Practice with VMware Tanzu by Parth Pandit & Robert Hardt(3629)
Windows Ransomware Detection and Protection by Marius Sandbu(3603)